How to become HIPAA compliant on AWS in 2022?
Since the 90s, when you run a company in the Healthcare industry in the US market, you must comply with the Health Insurance Portability and Accountability Act (HIPAA) Security Rule. Some of the security rules are directly linked to how you operate your organization, the others how you manage your application data for your customers. This article will walk you through what to consider on AWS to be HIPAA compliant in 2022.

Romaric Philogène
January 19, 2022 · 4 min read
#The challenges
Building an infrastructure HIPAA compliant on AWS is challenging. You need to properly manage your application data’s logical and physical isolation for your customer. AWS provides all the layers of security you need to integrate into your technical stack and organization but require to have one or more people dedicated to the setup and maintenance of those services.
Here is a non-exhaustive list of things you need to consider to be HIPAA compliant on AWS:
- Limit and audit the AWS access with Cloudtrail
- Isolate your compute (EC2) resources with different VPC
- Use KMS or equivalent to manage your secrets
- Encrypt your databases
- Define a proper backup and recovery strategy for your databases
- Etc…
Let’s dig into the most important aspects to consider.
#Multi-tenant application isolation
Not directly related to AWS, you need to isolate your users from each other inside your application correctly. Did you have all the proper unit and functional tests to validate that a user X can’t access the data from a user Y?
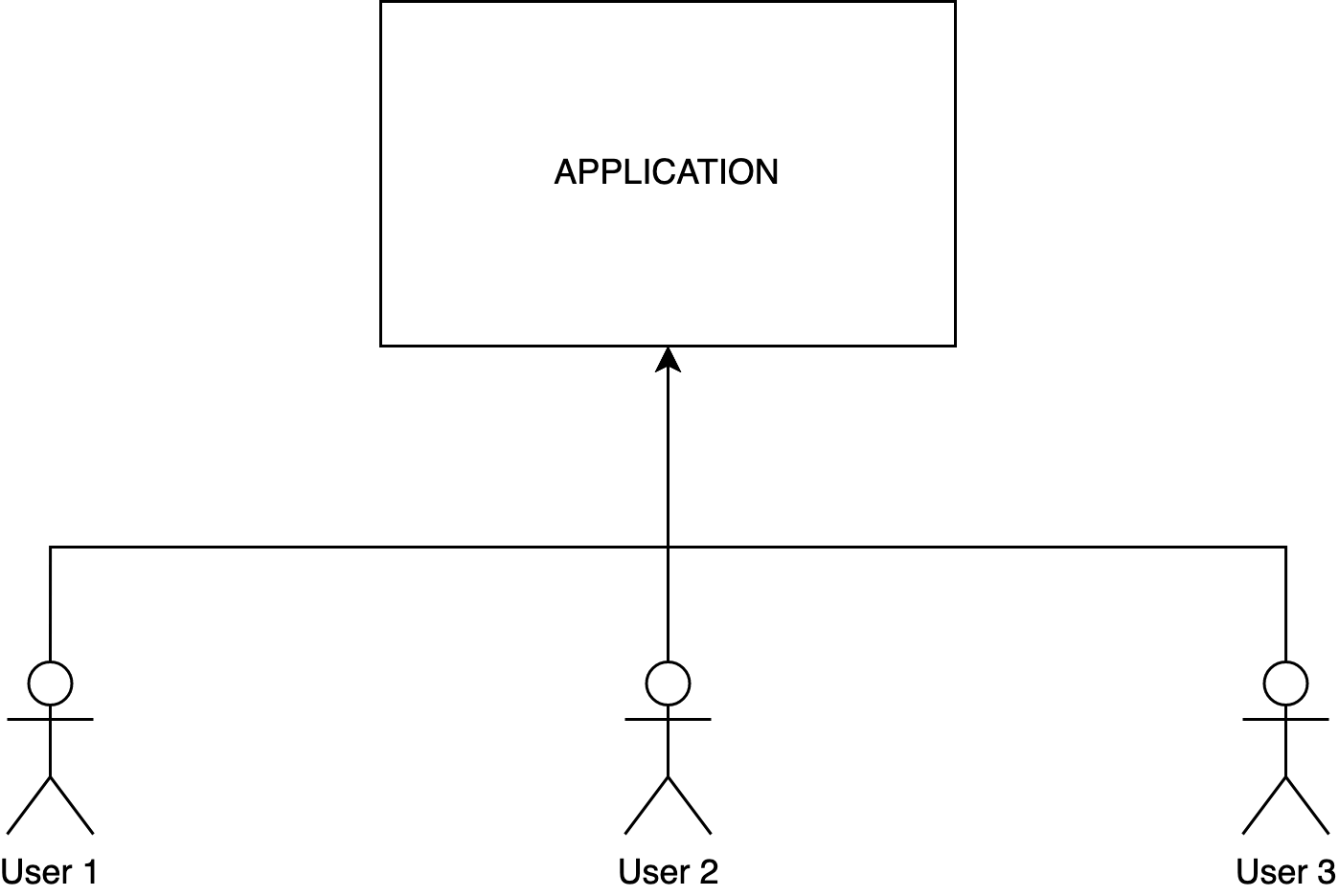
You need to make sure that no other users that the permitted one can access the data from another one. Using a vulnerability scanner tool is also good to ensure no well-known uncorrected security breach.
#Single-tenant application isolation
In the single-tenant application configuration, every user gets their instance of your application. Meaning they are isolated from each other at the process level. It is state-of-the-art isolation but requires extra cost in hosting and management. You need to think about how to handle the upgrade of your fleet of applications.
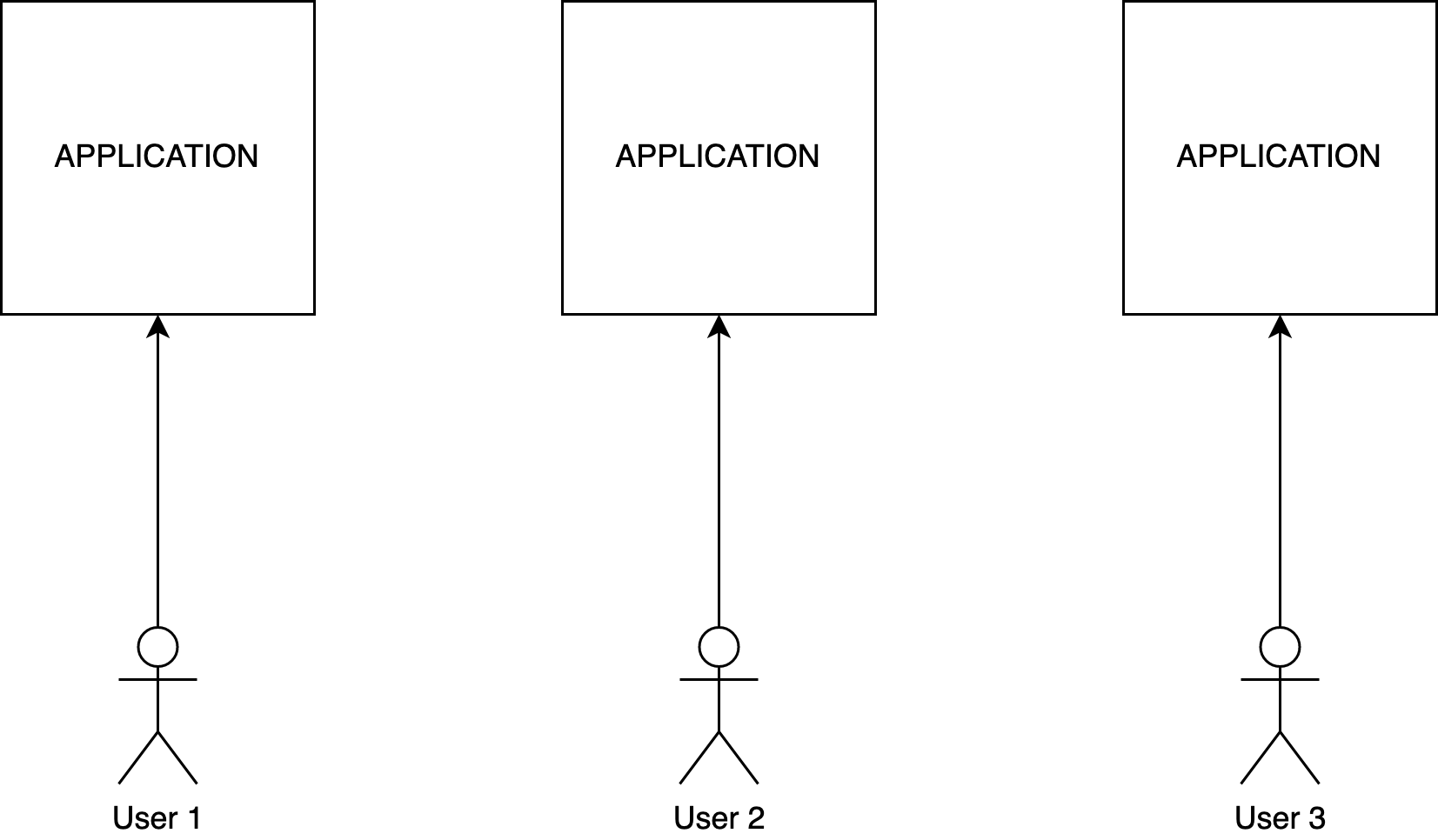
Consider using Virtual Machines instead of containers. A container does not have the isolation property of a Virtual Machine. By using a container, a compromised application can access the host kernel and then compromise all the other applications running on the same host. An AWS EC2 instance is a virtual machine. You can even run a container in an EC2 instance with ECS, Fargate, or EKS.
#VPC isolation on AWS
AWS provides the concept of VPC that lets you keep isolated the network of every customer, which is an excellent practice in a single-tenant application scenario.
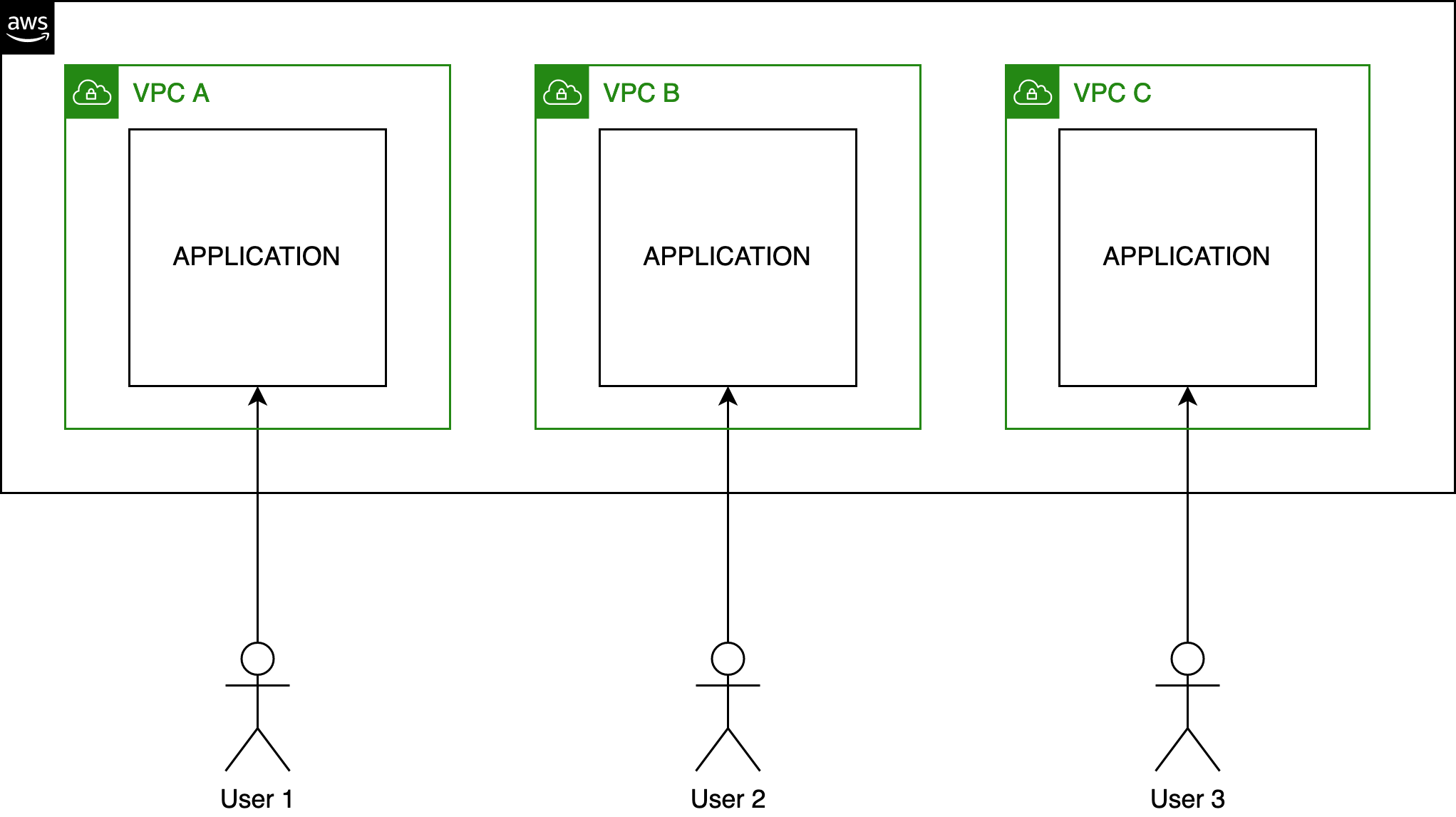
It is also possible to explicitly allow the VPC A to exchange data with the VPC B. It is all about VPC and basic network routing configuration.
If you consider using a multi-tenant application configuration, using VPC isolation between your users is impossible.
Important Note: AWS limits the number of VPC to 100 per account. You will need to have multiple AWS accounts to go beyond this limit (easy to do with Qovery).
#Database encryption and backup
Needless to say that your database data needs to be encrypted. The goal is to avoid any data leak in case of a physical breach attempt. A malicious individual will not be able to do anything from your encrypted data. AWS RDS and other managed AWS databases provide built-in encryption at the storage level.
Database backup is also required to be HIPAA compliant. Turning on the backup feature with an AWS-managed RDS is straightforward and convenient in data loss.

If you are in single-tenant application architecture, you will need to manage for every single application a dedicated database.
Important Note: Your database must not be accessible from the Internet. Using a secured bastion/bouncer is a good practice.
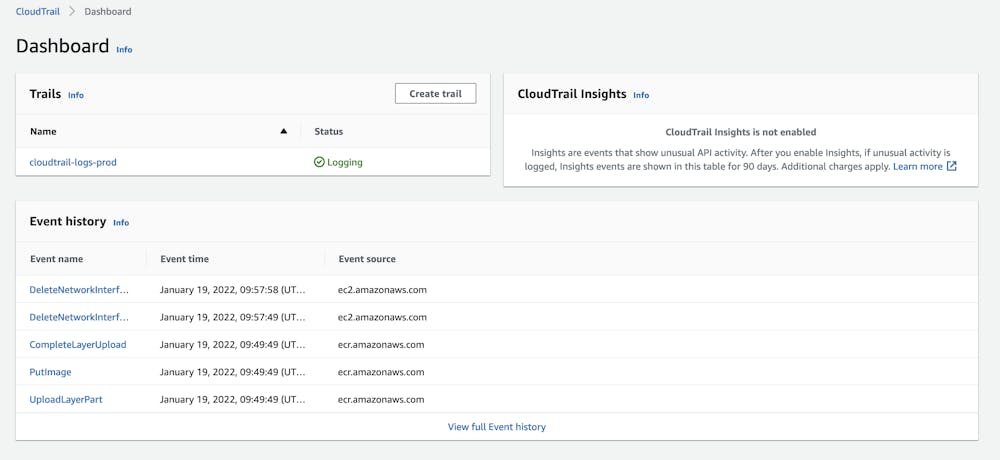
#Accounting with Cloudtrail
HIPAA requires that you track down who gets access to your application and your customers’ data. AWS Cloudtrail tracks every single access to your AWS account and the different services. It is a must-have to be HIPAA compliant and be covered in case of a security flaw.
#Two-factor authentication
When it comes to HIPAA compliance, verifying authorized access requires more than just knowing a username And password combination is mandatory. Two-factor authentication (2FA) must be implemented at your organization level and enforced for every user of your organization. Then, even one of your team who lost his credentials will not be exposed to a usurpation.
#Secrets encryption
AWS KMS and equivalent like Hashicorp Vault helps you keep safe all the secrets your application and organization use to access sensitive data. Using a secret manager is perfect practice and required to be HIPAA compliant.
#Conclusion
This article has covered the most important aspect you must consider to be HIPAA compliant on AWS. Even if it can be seen as a constraint, those points are excellent practices for security for your organization and your customers. The sooner you consider implementing them, the easier it will be.
---
Your Favorite DevOps Automation Platform
Qovery is a DevOps Automation Platform Helping 200+ Organizations To Ship Faster and Eliminate DevOps Hiring Needs
Try it out now!

Your Favorite DevOps Automation Platform
Qovery is a DevOps Automation Platform Helping 200+ Organizations To Ship Faster and Eliminate DevOps Hiring Needs
Try it out now!